
Information Security Day – Focus on InfoSec
We interviewed Ryan, our Cybersecurity lead and Senior Technical consultant to gain insights into staying safe at work and online. He guides our procedure and policy development here at JPSys to help them align to the ISO standard’s requirements. He does due diligence on scanning for vulnerabilities and performs remediation for information security systems. In this blog Ryan gives us insightful background on Information Security and Cybersecurity concerns, what the future holds, and how to best protect yourself and your organization.
Information Security and Cybersecurity have been a focus as long as information networks have existed either by foot, horse or cart, as even in ancient times there have always been intrigue and espionage. With the evolution of technology and the interconnected world, people everywhere are becoming more aware and affected by security breaches. Security processes start with identifying risks around information and data. How could a leak occur? How could someone gain access to information they should not have? What would the implications and consequences be and how should you respond if an incident happens? How do you contain situations and how do you prevent them? Our policies and procedures need to address all possibilities. To help us with this, we follow international standards for Information Security (InfoSec) and Cybersecurity to be sure nothing is left out.
Security Standards
There are different approaches to implementing Cybersecurity with ISO being one of the largest sets of standards and guidance companies aim for. Organizations can create their own individual policies to fit their situations and business needs. There is a plethora of rules regarding security with which organizations need to comply. Some of these interactions are specific to, for example, health or defense systems. Regulations and rules regarding security which individual organizations must follow are dictated in part and based on the types of data they collect. This can include clinical information. With both health information and Personal Identifiable Information (PII), like a date of birth or a social security number, you must identify and catalog any risks that may lead to the exposure of that information. You must take security a step further and consider securing any information that may surround that information to give someone leverage to be able to get the PII. Then you must develop an action plan for a response.
What is the difference between Cybersecurity vs. Information Security?
The primary difference between information security and cybersecurity is the role of technology. Cybersecurity involves the safety of computer systems, and everything contained within them, which includes all things digital data. In contrast, Information Security, which is defined in detail by the ISO standard 27000 family, refers to the safety of information in all of its forms, whether or not stored in a computer system. Cybersecurity is a matter of securing digital Information Systems. Information Systems contain items in cyberspace and beyond which interact with cybersecurity such as phones, laptops, databases, and networks.
Best Practice for Keeping your Information Secure
Start understanding what your exposure is by looking at your online presence. Google your name and do your research to learn more on data brokers and how to remove your information from data brokers. This data, and metadata about you is what is accessed with Information Security breaches. Any information online may be a personal risk. Metadata is peripheral information about you that is easily accessible to anyone who may have some knowledge about you such as high school mascot, last visit to a certain location, your cell carrier, et cetera. This is information on who you are and what you do to build a profile. Do not expose unnecessary information online. When it comes to passwords, a book of passwords is not necessarily a security risk. As humans we know how to secure physical items. You can more easily secure what you see. Because you can’t easily secure what you can’t see, find a trustworthy, reliable solution for keeping passwords safe and secure, and learn how to create a great password or randomly generate one.
Cyber Security and Information Security is Important Because …
We will only ever become more and more connected online, and attacks will increase in sophistication and pressure. It is important to be aware of these risks and stay ahead of the game by knowing the most common scams such as:
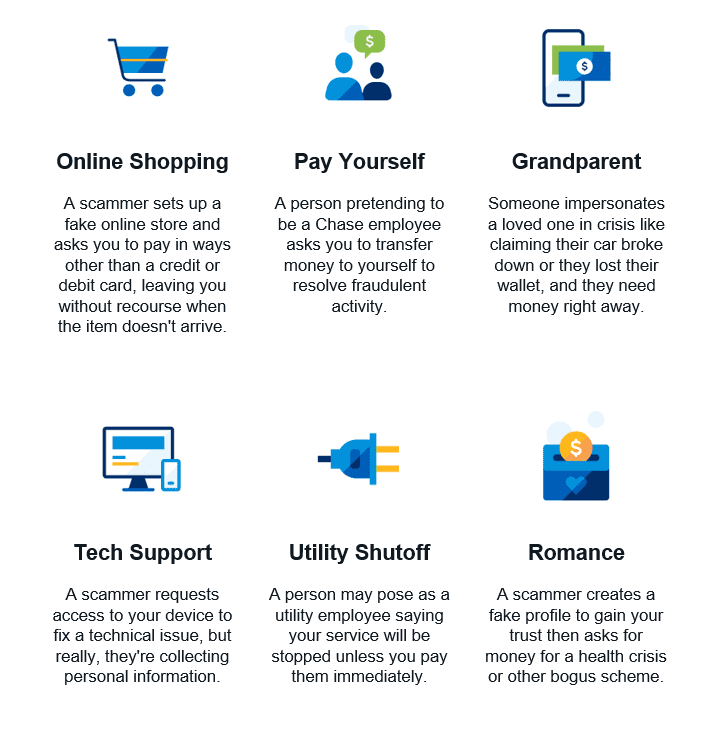
Currently, a lot of attacks are first targeting individuals to gain access to organizations. Don’t rely on mainstream resources as a way to get your cyber security and information security news as they are sensationalized and often oversimplified. Search for security experts who have direct interactions with the security community by doing things or reporting. The more you see the more you will learn and determine what sources of information are useful and will keep you safe.
Here are some great resources for Cybersecurity:
Bruce Schneier: https://www.schneier.com/,
Brian Krebs: https://krebsonsecurity.com/,
Steve Gibson: https://twit.tv/shows/security-now
https://www.grc.com/securitynow.htm universities that have cyber security programs.
